
<aside> 💡
Build your own CTI by deploying OpenCTI—seriously, and on a budget
</aside>
At Crimson7, I found myself needing to delve into Threat Intelligence. A quick internet search revealed that OpenCTI is rapidly emerging as the leading platform in this field.
The beauty of OpenCTI is that it allows you to collect, ingest, and correlate data, as well as automate processing to present and consume aggregated data from different sources in the way you want. At C7, we're focused on threat-informed security. Rather than just IoCs and millions of indicators to consume in a SoC, we need to understand how actors operate and what TTPs (or Attack Patterns, to use OpenCTI terminology) are used in campaigns and attacks. We're after Attack Intelligence—we're rebuilding these attacks. Let's wrap up the corporate talk with one last piece of info: if you're planning to dive into CTI and are looking for an open (hopefully for a long time) and beautifully engineered platform, consider this—Filigran, the company behind OpenCTI, just secured a Series A funding of $15 million.

OpenCTI can be easily deployed using Docker containers. It's straightforward: just browse the documentation, fetch the docker-compose.yaml file, and customize the .env file. However, a real deployment should consider two key factors:
This is the architecture of OpenCTI, it’s built on:
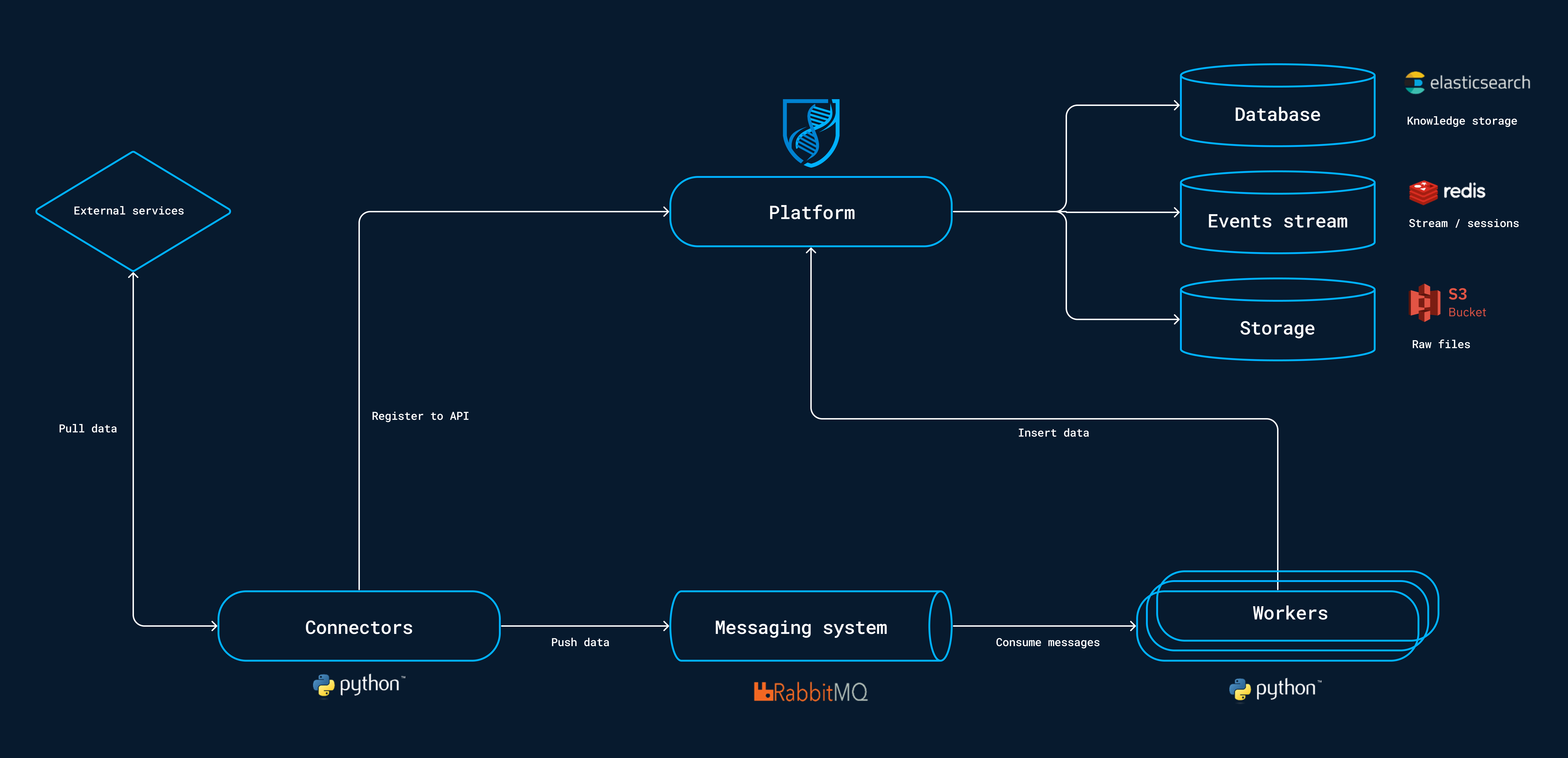
(image from the OpenCTI documentation)